Malicious Code: Serious Business
Viruses and malware are arguably are one of the biggest threats to our way of life in this country. Wow, dramatic stuff eh?Right now we are in the glorious period of Internet Utopia where everything and anything can be found online, but as we all know from our experience with human nature, where there is money to be spent and made, there will be those who go about it dishonestly.
In fact, one the foremost major concerns for the US Government and major CyberSecurity firms are organized "Cyber Attacks" such as a DOS (Denial of Service): An infection that comes in through one of the methods I will mention below, typically called a BOT and instead of throwing up adds based on your website history (like Malaware), this little software program is what opens the door for malaware, spyware, and very serious malicious tools that can often stay under the radar, install other programs, and consume system resources. However, it's the scary fact that they can also unknowingly "slave" your computer into doing things without your knowledge!
So, (and this is reality) imagine millions of computers infected with a particular bot that's been waiting like a "sleeper cell" to carry out it's mission, which is not being caught by your Virus/Malware protection since many folks don't scan specifically for this type of threat; They lay dormant, until activated and suddenly the machine is completely taken over (sometimes without the user ever realizing it) and takes over your email account and other programs, and with the army of those other millions computers, brings down an entire website from what I can only liken to a bolt of lightning hitting a transformer.
The good news is that tech insiders and the folks at major cyber security firms, the US Government under Homeland Defense oversees counter cyber threats and ranks the current Cyber threat level.
They could probably be doing more to educate people, but that is a subjective statement at best. What I believe they do understand is that these type of attacks arguably make up for the biggest threats we face as a nation from a terrorism standpoint and (our entire infrastructure is connected to computers) a work together with industry insiders to combat those who would do us harm and use their knowledge for evil. (Note to prospective College Students: Forget I/T as a degree, the need for I/T people will reduce significantly over the next few years. Cyber Security is where it is going to be at in this century.)
So, why is this important to you? It is important, because much like "see something / say something" (fundamentally) we are all responsible for protecting ourselves and making sure we understand the different type of computer related infections, what needs to be done to prevent them, and how the dynamics are changing. Furthermore, it doesn't have to be difficult or inexpensive!
What types of Malicious Software Should I be Concerned About?
Bots, Warez, Spyware... oh My!Well, we've all heard the different terms. Here's a great summery of the different types of infections which are currently out there. Jimmy Ray Purser explains it nicely.
Staying Safe / Methods of Protection / Tips Part 2 (Part 3 will have additional information. You can also contact me for a free assessment)
While there are a ton of software providers out there offering "system cleaners" and "Full Service Protection" at varying pricing levels. As I have mentioned before, for every one of those "paid" services, there are 3 free/alternative to subscription model methods that can minimize your investment.Firewalls
Don't let a program change your firewall exceptions unless you know for sure it's safe. Part 3 of this series will have my specific recommendations, but check out this video from Jimmy Ray Purser to find out exactly what a firewall does!
Email - Email - Email
When you receive an email with pictures in it, that photo is stored on a website and your email program has to go get it. Not only does this open you up to downloading something unintentionally, it's also the way marketers track whether you open, read, delete, or respond to an email. Set your email program to only download pictures from safe senders (people you trust).Spoofing/Phishing
Often, because it's easier to create a domain and an email address that looks similar to the real thing, and even post a fake website that looks exactly like the real thing, Spoofs are a huge way to get hacked as they are looking to collect sensitive information by tricking you into filling it out. Everyone has come close to this I believe, as they look very rule. If you remember the tips below, you'll be WAY ahead of the game.Here is an example of a spoof below (Click on Photo for additional information on spoofing):
 |
| CLICK ON PICTURE TO READ ARTICLE |
These are what you want to check:
- Look at the email header or url (if you clicked to open it): It may be very close (e.g. mail@facebook.com vs. mail1-facebook31@mail.facebook.net. Remember, anyone can change the FROM to what they want or setup a domain (e.g. www.faceboo.com - they go after spelling errors often). If you suspect the email is a spoof, you should contact the institution.
- Does it say Dear Customer or does it have your first or last name? Spammers buy email addresses or use programs that just mass send to different variations on domains, so it's rare to get a spoof that says Dear Joe/Jane from a spoofer . THIS IS ONE OF THE BIGGEST INDICATORS
- No reputable company will ever ask you for your SSN or CC/Banking Info (And the spammers are wising up to that, which is why they have you go to a fake web page).
- Check out sites like SNOPES.com who validates internet fact and fiction
Downloading and Opening Files
Probably the most common way of getting viruses these days is through downloading a file be it email or via the Internet.
For email, it's pretty well known you don't open any files from anyone you don't know, and never anything that is an executable (like an .exe file). Also, since people often get their accounts hacked, being vigilant on what you do open is critical. Always DOWNLOAD the file from the email BEFORE opening and THEN right click to scan with your virus scanner. (some email programs do this automatically, but it can't hurt. If you don't know, Google is your friend
WEB
Even I've gotten caught up in this one lately. Freeware or trial-ware can be a double edge sword, as companies like downloads.com have gone to a system that basically trades you a free program, and tries to slip things like TOOLBARS (Toolbars are virus magnets and completely unnecessary these days)
You can usually find the actual file with some digging but this is again where it's critical to SCAN your file before opening or unzipping. The download managers even try to give you reasons why they need to be a "middleman" between you and the file that you want. The trickiest one I've seen was a program where if I didn't click under advanced options (which usually gives you specific things related to the program setup) I would have never seen that the advanced options were INSTALL TOOLBAR, SET MY HOMEPAGE, ETC.
THIS IS THE MOST IMPORTANT ADVICE I CAN GIVE - READ BEFORE YOU DOWNLOAD. YOU DON'T NEED A TOOL BAR, YOU DON'T NEED TO CHANGE YOUR DEFAULT SEARCH PROVIDER, YOU DON'T NEED ANYTHING EXCEPT WHAT YOU ARE TRYING TO INSTALL
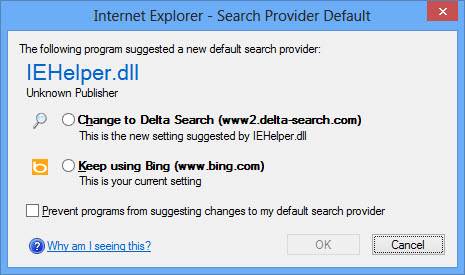 |
| EXAMPLE OF VIRUS INSTALL |
Stay tuned for PART 3: SimpleAssist Program Tips!



